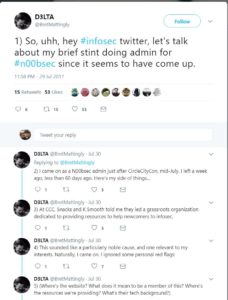
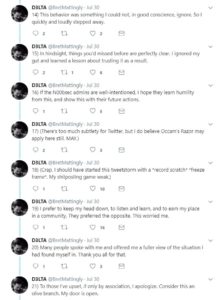
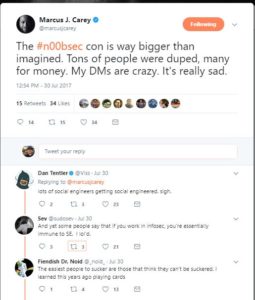
After some friends complained they also got screwed over, I felt it was finally time to write about a trainer that has wronged many.
While looking for some reasonable training, I found Joe Mccray, Strategic Security, that seemed to be supporting the community and offering inexpensive rates. I even spoke with a local person that had worked with him as a “Security Rookie” who said good things. Despite my better judgement about paying for semi-intro classes, I decided to try a class. I learned to trust my judgement more on training.
I signed up for “Catch Me If You Can: Bypassing AV/HIPS/NIPS Online Workshop” in August of 2013. This was supposed to run noon until 4pm on August 17th and 18th. I confirmed regardless of the errors on the initial email sent as well as the fact video’s of both days would be sent.
At the end of the day, he sent out a txt file with some of the commands used and promised he would send out the videos shortly. He also sent information created by a group called Web Application Security Consortium. These were solid resources albiet being a few years old at the time of distribution.
At the end of the first day, he sent a invite to the second day with the wrong times listed (he had noon until 10pm instead of noon until 4pm). Regardless, I confirmed again the times for the following day and asked when he would release the video for day 1. He confirmed the times for Day 2. An hour before Day 2 was scheduled to start, he sent a email:
“I’m sorry to have to do this on such short notice. But I’m leaving for the airport right now. I have to help a customer with a compromise so I will not be able to run this class today. Please accept my sincerest apology as I know several of you are in other timezones and that makes attending this workshop very difficult. I promise I will make it up to you.
Again, please accept my apology and I’ll see you next week.
BTW…yesterday’s video and class notes I’ll take care of sending to you when I get off the plane and get to my hotel later tonight.”
I was annoyed, but didn’t make a big deal of it as emergencies can happen. He sent out a invite for the following week with again the wrong times (he had noon until 10pm instead of noon until 4pm). On 8/26, the supposed make-up day, he didn’t show up. A few days later, I emailed and again asked for the video’s from day 1 and when the makeup would occur.
Rather then complete the session promised, he decided to replace day 2 with another class he had made. This one on a completely different subject and during the week instead of on the weekend like the original. So two weeks after the class was supposed to have occurred, he never sent out the rest of the info from class 1 and never had class 2. He also had only offered to move into a different class.
The make-up class he offered got pushed back a additional week as well. Then he ended up canceling class one of the days due to a “network outage”.
I still have yet to receive the video from the first class and have long since given up on it. I told him the way things were handled were poor at best with no response. Over the 1.5 years since, dozens of people have told me similar stories of being severely disappointed with his unprofessionalism. One of his own friends went as far as to apologize to me and tell me Joe is a good person, but a “terrible person to do business with”. I have heard numerous stories from friends that he repeatedly cancelled classes, didn’t share materials and was just generally unprofessional considering he is charging money for his trainings. I have encountered numerous trainers that have been significantly more professional in free classes then he was in classes he charges money for.
Additional instances of people publicizing their issues with his content or teaching:
- A significant portion of the content from a paid webinar were stolen from Exploit Lab without credit or permission (see: http://blog.exploitlab.net/2013/02/defending-our-work-part-2-exploit-lab.html ) as well as covering some of the concepts incorrectly.
Some of the comments show the kind of person Joe is and the type of work you can expect from him:
- “msploit12 February 2013 at 12:52
I’m incredibly happy to hear someone has finally outed strategicsec. Over the past year I’ve watched a lot of things unfold with Joe McCray. You just have to look at his security rookies ‘program’ to understand what hes up to. His unpaid ‘rookies’ have in many cases preformed recon for actual pentests. Hmm unpaid people doing for the benefit of a company, yep thats a violation of labor laws. I also have personal knowledge of Joe linking to and hosting pirated books and courseware for his ‘rookies’ and other people. He also has his ‘illegally unpaid’ rookies put together some of his class material which is sold.”
- Another former ‘rookie’ commented:
“throw away13 February 2013 at 00:25
As a former ‘rookie’ I can attest to this. Under the guise of giving us ‘real world’ experience he is essentially getting free labor and charging the clients for his (really our) time. Rookies are tasked with creating his training material which usually involved him providing a ‘rough draft’ and us fixing errors and importing it to his letterhead. Often, when having to research the problems we found that the material was pirated from SANS reading room, GIAC Gold papers, or other publicly available sources with no attribution to the original source or author. There was some original content generated, but it was far and few between and almost always created by unpaid ‘interns’ that was in turn sold through his training programs.”
- Another former ‘rookie’ said via Twitter DM when asked about the program:
“I bailed pretty early. After a couple weeks of working for free, I stopped. It was obvious he was just trying to take advantage.”
- More Recently, someone commented some more issues ( http://nathanheafner.com/home/2014/02/17/in-depth-and-personal-infosec-training-thats-affordable/ – sadly the comments show mixed results )
**Update – Nathan’s site seems to have gone offline so I swapped to Wayback Machine
“Michael • 2 months ago
You must have got in early. I’m in the middle of taking a class with Joe now (Pentest candidate program). He advertised the classes as being Monday and Wednesday, 7-9pm for December-February. However he has already cancelled 7 classes, and most of the other ones were only about an hour in length. Some members of the class are saying it’s a scam, others are saying he’s just winging it.
Either way, I would strongly advise anyone against taking classes with Joe.”
- A friend that was in the Security Rookies program said that Joe used them to write his material and do unpaid work for his company. You can get some experience, but at the cost of being used.
Someone from CarolinaCon adamantly defended Joe as he was criticized on Reddit
While Joe may be knowledgable, I compiled these stories so people understand what they are getting into. If you are looking at the Security Rookies Program, there are people that have gotten a lot from it, but it is at the cost of being used. Some people have had a positive experience… While I am bitter and would never do business with Joe or recommend anyone else do so, he is knowledgable and he has given opportunities to some that are not easily obtained…
=====================================================================
A friend just shared another story with me:
On December 1st Strategic Security will launch the Pentest Candidate Program. This program is designed to satisfy the basic requirements to be a penetration tester. The program covers the common technical requirements, common soft skill requirements, and via a partnership with several penetration testing firms the top candidates will be given job interviews at the end of the program for a remote penetrating testing position (remote meaning you can work from home).
If you already have a US Security clearance, currently live in the DC, Maryland, Virginia area and you are one of the top candidates you may be given the opportunity to interview for a cleared penetration testing position.
This is your chance. If you REALLY want to become a penetration tester then this is the perfect combination of training, mentorship, and opportunity.
What is covered in the program?
This program is hard, but rewarding. It covers the following subject areas:
Command-Line Kung Fu
Linux Command-Line Fundamentals
Windows Command-Line Fundamentals
Network Penetration Testing
Scoping a penetration test
Performing a penetration test
Reporting penetration test findings
Web Application Penetration Testing
Scoping a web application penetration test
Performing a web application penetration test
Reporting web application penetration test findings
Python For InfoSec Professionals
Log parsing with Python
Pcap parsing with Python
Network testing with Python
Web App testing with Python
Preparing for a job as a Penetration Tester
Resume assistance
Assistance with building a portfolio based on this program
Mock interview
Interviews with up to 15 Penetration Testing firms for top candidates
Interviews with up to 5 DoD contractors for top cleared candidates
How is the program delivered?
On Monday of each week you will be assigned a set of tasks that required to be completed by Sunday at midnight EST. These tasks usually include:
Required reading
Required videos to watch
Required lab exercises to perform
On Mondays and Wednesdays from 7-9pm EST a live online training session/QA period will be held. The sessions will be recorded each day so you do not have to worry if there are scheduling issues.
The program will run from December to February (3 months) with job interviews for top candidates being held in March.
The program cost is $150 per month for 3 months, or $300 as a 1-time fee for the program.
This class is only $300 so signup now!
Example on how he still cancels classes.
Guys, I am really sorry but I have a family emergency to tend to. I will double the length of tomorrow’s class to cover for tonight.
He claimed he had partnerships in his advertisement email:
The program covers the common technical requirements, common soft skill requirements, and via a partnership with several penetration testing firms the top candidates will be given job interviews at the end of the program for a remote penetrating testing position (remote meaning you can work from home).
Preparing for a job as a Penetration Tester
* Resume assistance
* Assistance with building a portfolio based on this program
* Mock interview
* Interviews with up to 15 Penetration Testing firms for top candidates
* Interviews with up to 5 DoD contractors for top cleared candidates
Participants commentary on that:
As part of the class…he advertised that the students in the DMV area could get jobs afterwards if they performed well in the course. The only thing he did in that regard was have HR professionals present the skills and credentials they look for when hiring infosec people. It didn’t appear that he really had jobs for these students….instead…just provided some information on how to get jobs (which is far from the same thing)
Your first challenge:
Use the OSINT_Innophos doc as a reference and perform/document an OSINT assessment against any one of the following companies:
NSA
HSBC
Coke
Exxon Mobil
KPMG
Accenture
NewYork-Presbyterian Hospital
Kroger
Dillard’s
Royal Caribbean International
Tools
Here are some tools that I think you should consider using for this challenge:
FOCA
Maltego
Search Diggity
ShodanHQ
Firefox PassiveRecon
EDGAR
theHarvester
gxfr.py
VisualRoute
Recon-NG
Now I am not a pen tester, but suggesting people preform OSINT on the NSA is a really bad idea, even passive recon. The last block quote was straight from an email from Joe.
We didn’t receive feedback on their OSINT assignment. I don’t want to assume….but…I would guess that McCray probably rarely hands out feedback (but..thats an assumption and not based on factual evidence)… I help with OSINT report around 12/6-12/14 on a company. Used google docs. I dont know how well we did.
The PPT attachment shows Joe canceling 4 classes (assuming I counted correctly) and he asked the students to help him with one of his *real life pentests* Im assuming he was doing for his business.
The Hangout is a chat with the people in the class. It first starts off with everyone trying to solve problems together and quickly takes a turn where people are asking if class will ever be held again.
No feedback on the sketchy assignment. Canceling ~15% of the classes; 4 classes out of 26. He had excuses each time, but after reading all the various stories, I keep hearing about cancellations including 50% of the classes I had with him.
Update 12/20/2019: I got a twitter DM about a new CEH class story via Security Ninja
I’ve been in a course with Joe McCray this week and came across your blog post. Do you still hear concerns over his material? Some things feel a little fishy and I wanted to reach out.
He gave us access to exam questions he’s purchased on vcetrainer.com. He shared his credentials with the class. This morning he gave us a copy of the exam, while taking the real exam. He instructed us not to finish faster than 90 minutes.
Class is through Security Ninja
If you wish to contribute a story, just submit it as a comment or send it to me, good or bad!